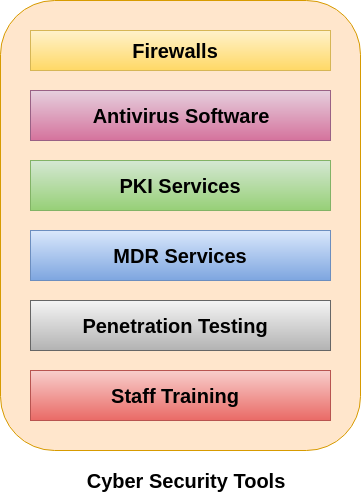
Aon India Insurance Brokers Private Limited - Critical infrastructure provides essential services and any service disruptions could have a significant impact to a significantly large user base. The maturity of security tools

GPACM: GUARD AND PATROL, ACCESS CONTROL MANAGEMENT (PROVIDE GUARD AND PATROL SERVICES AND OPERATE BASIC SECURITY EQUIPMENT) - LearningHub









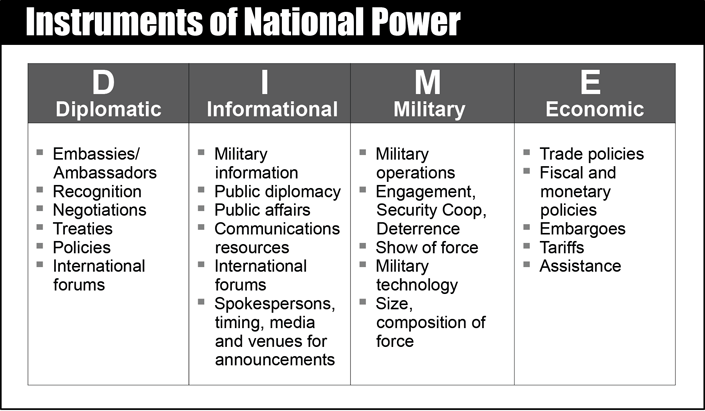



![PDF] CSIRT Basics for Policy-Makers | Semantic Scholar PDF] CSIRT Basics for Policy-Makers | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/cd352b579f47830c90fa4a9f10c49baee3bdbaf2/13-Figure2-1.png)
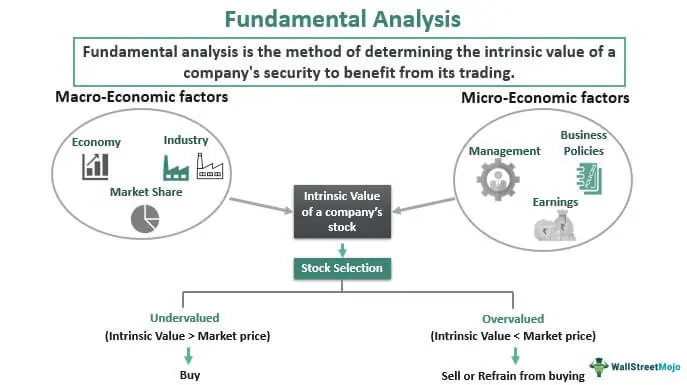
:max_bytes(150000):strip_icc()/asset-backed-security-4201381-1-bd07a6656c814548a785cc0eeb5ff1c4.jpg)



:max_bytes(150000):strip_icc()/Terms_s_security_FINAL-8dd9fbfea9004d4089e361976aa60aef.jpg)