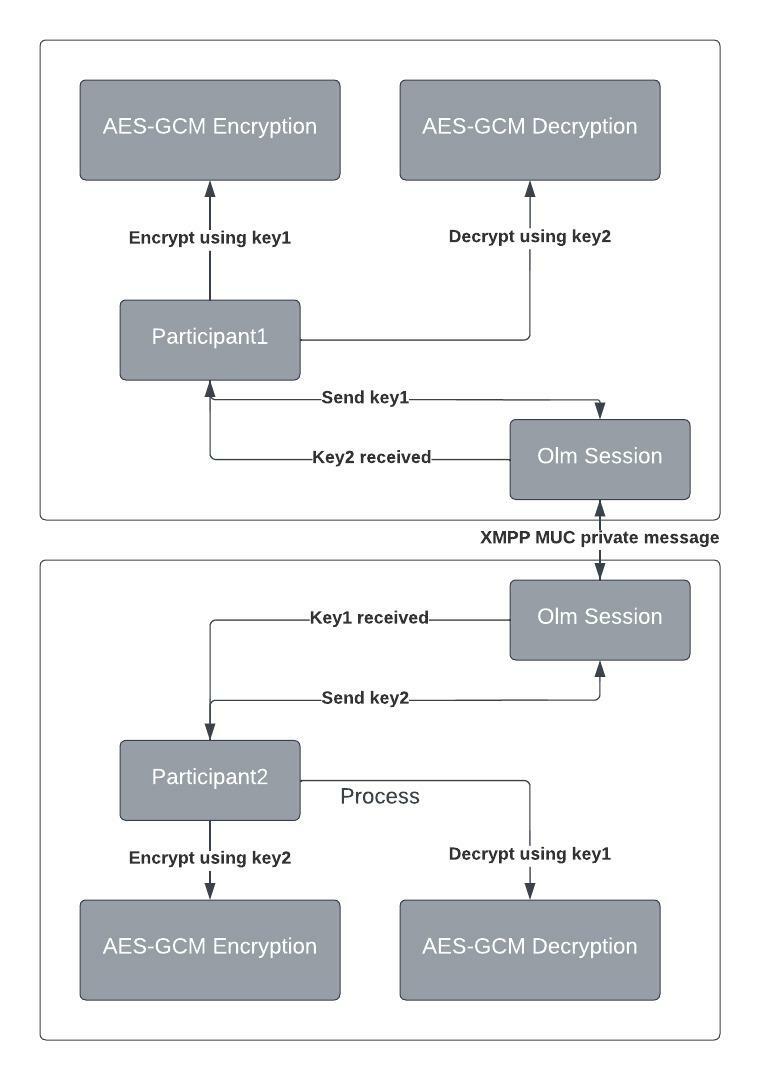
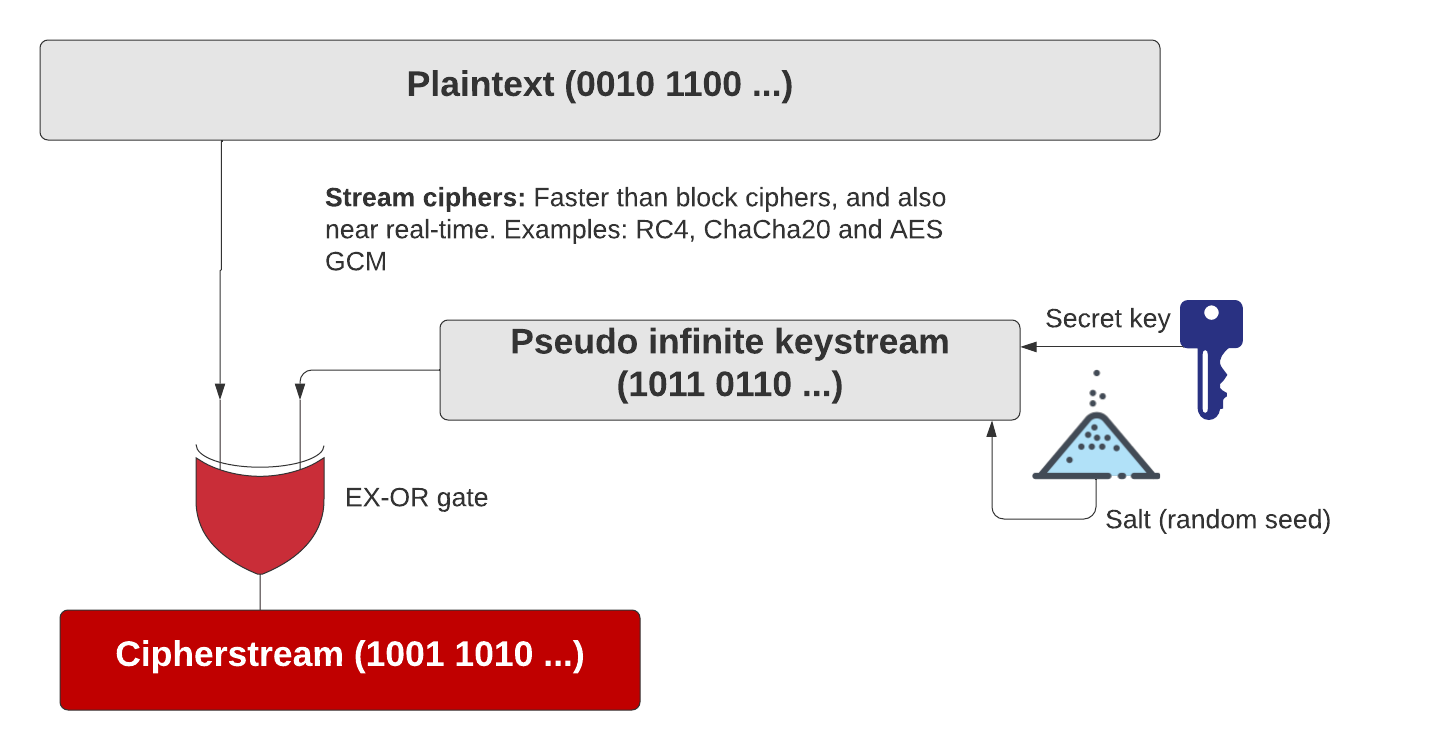
Zoom Finally Moves To End-to-End Encryption: And Takes Security Seriously | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium

Performance comparison of AES-GCM-SIV and AES-GCM algorithms for authenticated encryption on FPGA platforms | Semantic Scholar
Security Best Practices: Symmetric Encryption with AES in Java and Android | by Patrick Favre-Bulle | ProAndroidDev
GitHub - keygen-sh/example-python-cryptographic-machine-files: Example of verifying cryptographically signed and encrypted machine files using Python, Ed25519 and AES-256-GCM.